Servicing the Military as a Small Company in the Face of Increasing CMMC Regulations
 Cybersecurity has become a huge concern in modern warfare, not just on the battlefield. Protections are needed for technologies and entities well before tactical engagement. This blog focusses on Hydro Electronic Devices, Inc., journey to build-out a cybersecurity infrastructure robust enough to continue contributing to the multiplexing of military vehicles. We are a small mid-west manufacturing company located in Hartford, WI. Our vehicle controllers, human-machine interfaces, and telematics portfolio for monitoring, data collection and reporting are well known for flexibility and versatility. Throughout our history, this differentiation has facilitated adoption across a multitude of OEM markets, vehicle types, and applications. The portfolio is found on large construction machines, cranes, Fire & Emergency vehicles, transportation vehicles, and agricultural equipment, to name a few. Even though macro trends across the markets are similar (connectivity, electrification, security and varying levels or autonomy) in many ways the product requirements are diverging. Vehicles within a market space are at different states of adoption.
Cybersecurity has become a huge concern in modern warfare, not just on the battlefield. Protections are needed for technologies and entities well before tactical engagement. This blog focusses on Hydro Electronic Devices, Inc., journey to build-out a cybersecurity infrastructure robust enough to continue contributing to the multiplexing of military vehicles. We are a small mid-west manufacturing company located in Hartford, WI. Our vehicle controllers, human-machine interfaces, and telematics portfolio for monitoring, data collection and reporting are well known for flexibility and versatility. Throughout our history, this differentiation has facilitated adoption across a multitude of OEM markets, vehicle types, and applications. The portfolio is found on large construction machines, cranes, Fire & Emergency vehicles, transportation vehicles, and agricultural equipment, to name a few. Even though macro trends across the markets are similar (connectivity, electrification, security and varying levels or autonomy) in many ways the product requirements are diverging. Vehicles within a market space are at different states of adoption.
One space where we enjoy success is on wheeled military vehicles designed and built for the US Department of Defense (DoD) and our Allies. We have contributed content on nearly 80% of the modern wheeled vehicle models used by the US Military including multiple controllers on the largest vehicle contract in this space. Similar to other markets, experiments in autonomy and electrification are taking place at virtually all DoD prime contractors. But in this space, higher levels of security apply to vehicle control systems, vehicle data, and the organizations in the supply chain. It was not always that way. Small companies that may have lacked experience in MIL Standards, familiarity of trade restrictions, or the resources to develop programs and monitoring systems mandated of a prime contractor could still participate as a tier 2 supplier. The prime contractor provided a level of “insulation.” By delivering technological expertise valued by prime contractors we have been able to build mutually beneficial partnerships with military OEM’s enabling us to learn from their knowledge and experience gaining deep insights into these requirements. With the lessons learned, we have further invested in the journey to identify and close gaps as necessary to be a great OEM partner for those wishing to participate in lucrative military contracts.
Although there is an exemption for commercially available items, referred to as Commercial off-the-Shelf (COTS), since 2012 compliance with Defense Federal Acquisition Regulation Supplement clause 252.204-7012 (DFARS 7012), titled as Safeguarding Covered Defense Information and Cyber Incident Reporting, has been included in all DoD solicitations and contracts. The clause requires contractors to apply the National Institute of Standards and Technology security guidelines of NIST SP 800-171 (SP 800). The SP 800 provides a standard scoring methodology for a company to measure its level of compliance and for Government Agencies to compare the relative risks associated with potential contractors. Click here to get more information on the NIST SP 800-171 DoD Assessment Methodology.
Requirements have changed. Prior to November 2020, prime contractors were expected to voluntarily apply SP 800 in compliance with DFARS 252.204-2012. SP 800 requires the contractor to establish a System Security Plan (SSP) that describes in great detail the different layers of physical and cyber security in place to protect Confidential Unclassified Information (CUI). More recently, under DFARS 252.204-2019 (DFARS 2019) compliance is no longer voluntary. Companies wishing to compete for a contract award must attain a Basic Assessment confidence level by submitting the SP 800 directly to the Government. Any non-compliances existing in the SSP, as noted in the SP 800, require the contractor to have a Plan of Action and Milestones (POAM) to close those gaps. Even though we are not a prime contractor, we have attained our Basic Assessment.
Although the Basic Assessment is a self-assessment, compliance with DFARS 2012 and DFARS 2019 should not be taken lightly. The results of any level assessment are documented in the Supplier Performance Risk System (SPRS). Once submitted, under DFARS 252.204.2020 (DFARS 7020), the DoD has the right to review the SSP and POAM to determine compliance and assign higher confidence levels of assessment. An Agency may elect to come onsite and audit programs. Gaps in the SSP or incompletion of the POAM could prevent a company from participating in future solicitations.
An element of DFARS 7020 is the elimination of the insulation against standards and regulation that allowed small tier 2 or 3 suppliers to participate at arm’s length. In the normal course of business with a prime contractor, a supplier, including those that provide COTSs products, may receive CUI. To tighten security around CUI under DFARS 7020, prime contractors are required to push SP 800 further into the supply chain. Tier 2 suppliers must invest upfront in education and training necessary to develop a robust cybersecurity program and comply with the monitoring requirements around systems, data and facilities. These programs can be costly, so it is important to have a deep understanding of the requirements.
Only CUI requires heightened security, so a good starting point is to understand the difference between CUI and general commercial information. CUI is the unified term now used by all US Executive Branch Agencies to cover a range of information types and terms applied by these Agencies:
- For Official Use Only (FOUO)
- Controlled Technical Information (CTI)
- Covered Defense Information (CDI)
- Uncontrolled Classified Technical Information (UCTI)
- Sensitive but Unclassified (SBU)
 Some forms of CUI may not be obvious. Some companies tend to label everything as “confidential” even though the information does not meet the definition of CUI. Also, there is a level of subjectivity so it is possible CUI might not initially bear any designation, especially when embedded software is a part of the product. DoD CUI Program Training is a useful, easy to understand resource to aide in identifying CUI.
Some forms of CUI may not be obvious. Some companies tend to label everything as “confidential” even though the information does not meet the definition of CUI. Also, there is a level of subjectivity so it is possible CUI might not initially bear any designation, especially when embedded software is a part of the product. DoD CUI Program Training is a useful, easy to understand resource to aide in identifying CUI.
A contractor that has or may be exposed to CUI must take the necessary steps to create the SSP, develop the POAM, and complete a Basic Assessment by filing the SP 800. They will need to implement all the line items of the POAM and reach a score of 110 on the SP 800. Reaching this threshold will allow a company to participate directly for solicitations or make it more attractive as a potential sub-supplier in the supply chain.
Cybersecurity requirements are a continuum. Even companies that complete a review and attain a High Confidence assessment level under DFARS 7020 will be required to complete DFARS 252.204-7021 (DFARS 2021) Cybersecurity Maturity Model Certification (CMMC) by October 1, 2025. DFARS 2021 also requires CMMC Assessments to be repeated every 3 years. Under the DoD phased rollout, to be awarded some programs it may be necessary to attain certification prior to 2025. Specific programs are not yet designated.
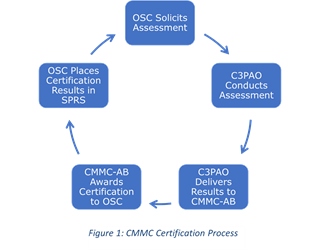
Clouding the path forward, the DoD has selected the CMMC Accreditation Body (CMMC-AB) but CMMC Third-Party Assessor Organizations (C3PAO) have not yet been identified. An Organization Seeking Certification (OSC) requires the C3PAO to complete an assessment and deliver the results to CMMC-AB. Prior to performing an Assessment, the C3PAO must first minimally attain a CMMC Level 3 Accreditation. Similar to DFARS 20, DFARS 21 requires flow down into the supply chain. Identifying and contracting a C3PAO is not yet possible, the list of OSC is growing, and the Assessment Process repeats every 3 years (See Figure 1). Wait too long to engage and opportunity will be lost.
The solution for us was to build upon the years of experience and insight gained through strategic partnerships with customers, suppliers, and 3rd parties experienced in industries requiring higher levels of cybersecurity. We routinely search out training and educational opportunities to validate programs and develop proven best practices. We facilitate collaborations with supplier and customer partners to ensure we can identify CUI and protect it throughout the supply chain. For us, the cornerstone of our multi-layered cybersecurity program is the ongoing training on process and utilization of tools put in place to protect information entrusted to us by thUS Military. Our continued success, and the ability of our customer partners to win future contracts in the Military Market depends on it. We have the experience, systems, and products that guarantee it.
More Blogs
No documents were found matching your criteriaMeet the Author
 Kevin Malliet is the Key Account Manager at HED,Inc. He is a graduate of Marquette University with a BSME. With years of prior experience in industries regulated by the Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF) and Homeland Security, Kevin has been serving HED’s largest OEM’s in markets including Military, Fire and Rescue, Construction, and Crane since 2017.
Kevin Malliet is the Key Account Manager at HED,Inc. He is a graduate of Marquette University with a BSME. With years of prior experience in industries regulated by the Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF) and Homeland Security, Kevin has been serving HED’s largest OEM’s in markets including Military, Fire and Rescue, Construction, and Crane since 2017.
